Losing or having one’s smartphone stolen can be annoying and sad; there’s no way around it. But taking precautions to secure your data and prevent thieves from taking control of your phone or online account can turn that disaster into straightforward convenience.
Here are the few things we would be exploring to help prevent thieves from taking control of your phone or online account
- Common Security Measures
- Their limitations
- How to Explore Hammer Security Application
- How to Activate Find My Device on both Android and iPhone
- Other antivirus software that can help prevent thieves from taking control of your phone or online account.
- Here are 4 basic security measures you rely on and why they aren’t enough to keep you safe online from scammers trying to take control of your devices
- Common methods scammers and hackers thieves use to take over your phone and gain access to your sim card for a Simswap.
- Here are 5 straightforward things you can do today to prevent thieves from taking control of your simcard and online account
- Wrapping up
You might confidently declare, “I have fingerprint security,” or boast about your password-patterned security block and 2-factor authentication. You may even rely on Facial ID. However, these perceived security fortresses can crumble with a tap or glance, giving Swavy thieves access to your data and online account.
Have you ever questioned how your phone could be hacked despite implementing these measures to prevent thieves from seizing control of your phone and online accounts?
In this article, we will cover what you need to know to prevent yourself from becoming a victim of simcard swap scams in 2024
Here are 4 basic security measures you rely on and why they aren’t enough to keep you safe online from scammers trying to take control of your devices
Fingerprint Security: Fingerprint security is a popular biometric authentication method used to secure smartphones. While it offers a convenient and quick way to unlock your phone, it’s not without its vulnerabilities. One of the primary ways fingerprint security can be bypassed is through high-resolution images of fingerprints. Phone thieves, who are adept hackers, can use these images to create fake fingerprints that can fool the fingerprint sensor. Some fingerprint sensors can also be fooled by using gelatin molds or even everyday items like play dough. If someone has physical access to your phone, they may be able to lift your fingerprint from the device itself.
To mitigate these risks, it’s essential to use a strong, unique password in conjunction with fingerprint security and to be cautious about where and how you use your fingerprint to unlock your phone.
2. Password-Patterned Security Block: Passwords are a common method of securing smartphones, but they can be vulnerable to attacks. One of the most common ways passwords can be compromised is through brute-force attacks, where hackers use automated tools to guess passwords by trying different combinations. To protect against brute-force attacks, using a strong, complex password that includes a mix of letters, numbers, and special characters is essential. Additionally, it’s crucial to avoid using easily guessable passwords, such as birthdays or common words, and to change your password regularly. Using a password manager can also help you securely generate and store strong passwords.
3. 2-Factor Authentication (2FA): 2FA adds an extra layer of Security to your online accounts by requiring you to provide two forms of identification: your password and a verification code sent to your phone or email. While 2FA is an effective way to protect your accounts, phishing attacks can still bypass them. In a phishing attack, hackers trick you into providing your verification code by sending you a fake email or message that appears to be from a legitimate source. To protect against phishing attacks, it’s essential to be cautious about clicking on links or providing personal information online. Additionally, enabling 2FA on all your accounts and using a different verification method for each account can help protect against account takeovers.
4. Facial ID: Facial recognition technology uses biometric data from your face to unlock your phone. While facial ID is convenient and offers a high level of Security, it has its risks. Hackers can bypass facial recognition technology using high-quality images or videos of your face. To protect against this, it is essential to use a strong, unique password in conjunction with facial recognition technology and be cautious about where and how you use facial ID to unlock your phone.
Common methods scammers and hackers thieves use to take over your phone and gain access to your sim card for a Simswap.

1. Software Vulnerabilities: Software vulnerabilities are weaknesses in a program that hackers can exploit to gain unauthorized access to your device. These vulnerabilities can exist in the operating system, apps, or other software installed on your phone. Hackers can exploit these vulnerabilities by creating malware or malicious code that exploits the weakness. To protect against software vulnerabilities, keeping your software up to date with the latest security patches and only downloading apps from trusted sources is pivotal.
2. Social Engineering: Social engineering is a tactic used by hackers to manipulate people into giving up confidential information. Hackers often use social engineering to trick people into revealing their passwords or verification codes. One typical example of social engineering is phishing, where hackers send fake emails or messages that appear to be from a legitimate source, such as a bank or a social media site, and ask for personal information. To protect against social engineering attacks, you must be cautious about who you share your information with and verify the identity of the person or organization requesting your information.
3. Physical Access: The most straightforward way to bypass security measures on a smartphone is to have physical access. If thieves gain physical access to your phone, they can bypass many security measures, such as fingerprint or facial recognition. To protect against physical access attacks, it’s important to keep your phone secure and never leave it unattended in public places. Additionally, enabling a remote wipe on your phone can help protect your data if your phone is lost or stolen.
Here are 5 straightforward things you can do today to prevent thieves from taking control of your simcard and online account
1. Hammer security application:
It’s okay if you haven’t heard of Hammer’s security application; if you have followed on from the beginning till now, well, Hammer Security allows you to enhance your phone’s Security by integrating the Hammer Security application into your device.
Here’s how you can use Hammer Security
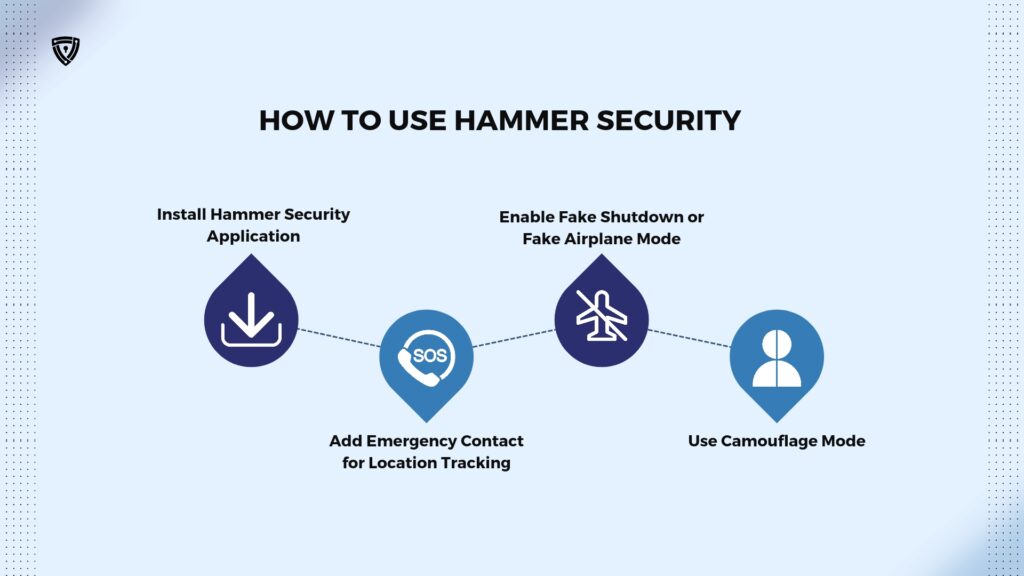
Install Hammer Security Application: Start by downloading and installing the Hammer Security application from the app store. Once installed, open the app and follow the setup instructions to configure it according to your preferences.
Add Emergency Contact for Location Tracking: In the event that your phone is lost or stolen, you can add an emergency contact in the Hammer Security app. This contact will receive your phone’s location information, allowing you to track its whereabouts.
Enable Fake Shutdown or Fake Airplane Mode: Hammer Security offers a feature that allows you to fake a shutdown or enable a fake airplane mode on your phone. This feature is useful if your phone is stolen, as it can fool the thief into believing it has been turned off. Additionally, when the fake shutdown or fake airplane mode is activated, Hammer Security can capture a selfie of the thief and send it to your emergency contact. This way, even if the thief tries to turn off airplane mode, the app will prevent it and continue to send updates to your emergency contact.
Use Camouflage Mode: Another useful feature of Hammer Security is its camouflage mode, which can make the app appear as a calculator on your phone. This helps prevent thieves from identifying and uninstalling the app. Using camouflage mode, you can discreetly protect your phone without paying attention to the security measures in place.
2. Enable Find My Device
Another phone-hero is FMD, (Find My Device). A faster approach to prevent thieves from taking control of your phone and online account is enabling FMD, as this is your rescue to saving the day one ping at a time! All you have to do is:
On Android: Open Settings, go to Security, and flick the Find My Device switch. For iPhone users, open Settings, tap your name, select Find My, and toggle on Find My iPhone.
Once you’ve activated Find My Device or Find My iPhone, you can locate your device on a map and take actions like locking it or erasing its data if it’s stolen. You can even set a message and backup contact number to be displayed on the screen when you lock the phone remotely. This way, if a good Samaritan finds your phone, they’ll have the info they need to return it to you.
However, be cautious; thieves can use your backup contact number to make phishing attempts. Stay alert and avoid clicking on suspicious links or entering confidential information on unknown websites. It’s better to be safe than sorry!
While losing your phone might be a hassle, taking these simple precautions can make the situation a whole lot more manageable. Spend a few minutes now to set up Find My Device or Find My iPhone, and you’ll thank yourself later if the worst should happen.
However, if your phone has been stolen,
For Android:
- Use Find My Device: Go to the Find My Device website on a computer or another device, and sign in with the Google account linked to your stolen phone. If your phone is turned on and connected to the internet, you should be able to see its location on a map.
- Use Google Maps Timeline: If you have location history enabled on your phone, you can use Google Maps Timeline to see where your phone has been. This may help you track down its current location.
- Contact your service provider: Contact your mobile service provider and report your phone as stolen. They may be able to track its location or block it from being used on their network.
For iPhone:
- Use Find My iPhone: Go to the Find My iPhone website or use the Find My app on another Apple device. Sign in with your Apple ID and password, and you should be able to see the location of your stolen iPhone on a map.
- Use iCloud: If your iPhone has iCloud enabled, you can use the Find My iPhone feature to locate your device. Log in to iCloud.com with your Apple ID, select Find My iPhone, and then choose your device to see its location on a map.
- Contact your service provider: Contact your mobile service provider and report your iPhone as stolen. They may be able to track its location or block it from being used on their network.
In addition to these steps, it’s important to contact local law enforcement to report the theft and provide them with any relevant information, such as the location of your phone, if you were able to track it.
3. Download Antivirus software:
Time to give those pesky phone thieves a virus they won’t recover from – the antivirus kind!
Downloading antivirus software is like giving your phone a health check-up and scanning for viruses and malware to keep it in top shape. Antivirus software serves as a protective shield, defending against hackers and ensuring the Security of your device and personal information.
But wait, there’s a twist: while Android users need antivirus, iPhones and iPads are immune to this digital ailment.
For Android users, knowing how to remove a virus from your device and selecting the best antivirus software are crucial steps in maintaining your phone’s Security. On the other hand, iPhones and iPads are generally considered more secure and do not require antivirus software.
It’s important to remain vigilant, as these devices can still be vulnerable to other forms of hacking.
Some Antivirus software you can download to prevent Thieves from taking control of your phone and online account :
Avast Mobile Security: Avast is a popular choice for Android users, offering a range of security features, including antivirus scanning, anti-theft tools, app locking, and Wi-Fi security scanning. It also includes features like call blocking and junk file cleaning.
Bitdefender Mobile Security: Bitdefender is known for its strong antivirus protection and low impact on device performance. It offers malware scanning, web security, anti-theft tools, and a VPN for secure browsing.
Norton Mobile Security: Norton provides comprehensive Security for your Android device, including antivirus scanning, malware protection, anti-theft features, and web protection. It also offers a variety of privacy features, such as app locking and Wi-Fi security scanning.
These antivirus software options can help protect your phone and online accounts from thieves by detecting and removing malware, securing your internet connection, and providing anti-theft features to locate, lock, or wipe your device if it’s lost or stolen.
4. Stay Safe on Public Wi-Fi:
Don’t let hackers catch you with your bytes down! When you’re out and about, connecting to public Wi-Fi networks can be risky. But fear not; a VPN (Virtual Private Network) is here to cloak your connection and keep your data safe from digital snoopers. A VPN (Virtual Private Network) is your shield against hackers, ensuring your connection remains private and secure when using unsecured networks in places like airports, cafes, and hotels. With a VPN, you can browse with peace of mind, knowing that your sensitive data, documents, and online activities are shielded from prying eyes. This level of protection is especially crucial given the amount of personal and professional business we conduct on our smartphones.
5. Backup your Data
Don’t let your data wander off without a guard! Setting up a backup is like stationing a digital security detail. Even if your phone becomes insecure your contacts and important information will be securely guarded and ready to download onto your new device. If you lose your phone, all you have to do is simply download a backup copy of the data onto your new device.
Setting Up Backup on Android:
- First, locate the System section in the settings. Afterwards, click on Backup. Then turn on Google Drive backup or select a computer or other outlet media as a target if your device offers that option.
Setting Up Backup on iPhone:
- To turn on iCloud Backup, follow these steps: Open the Settings app on your phone and tap on your account name. From there, select iCloud and then Backup. Ensure your phone is plugged in and connected to an unlimited plan Wi-Fi network, as the initial upload may use a lot of power and data. Check how much storage space you have left, and if you need more, consider purchasing a subscription from Apple or using a free alternative. Remember to lock your screen to prevent any accidental tap that might disrupt the backup process
Other Apps you can use to prevent Thieves from taking control of your phone and online account:

Cerberus:
- Key Features: Take control remotely, automatic alerts, precise location tracking, device locking, piercing alarm activation, capture intruder photos and videos, record audio, and automatic actions.
- Availability: You can get it directly from the official website with a seven-day free trial; plans start at just $5/month.
- Why Choose Cerberus: With its rich feature set and unmatched reliability, Cerberus stands tall as the ultimate guardian against theft. From locking down your device to capturing evidence against thieves, Cerberus offers comprehensive protection and peace of mind.
Anti-Theft Alarm:
- Key Features: Blaring alarm activation, remote alarm triggering, silent mode bypass, password-protected deactivation, battery and SIM change protection.
- Availability: Free to download and use.
- Why Choose Anti-Theft Alarm: Bright and bold, Anti-Theft Alarm is your audible shield against theft. Its loud alarms and smart triggers keep your device safe, alerting you and others to any unauthorized movements or attempts to steal your phone.
McAfee Mobile Security:
- Key Features: Secure device locking, thief cam snapshots, app uninstallation protection, wrong PIN snapshots, find my phone with map view, remote alarm activation, and step-by-step location tracking.
- Availability: Free version with premium upgrade options for enhanced protection.
- Why Choose McAfee Mobile Security: McAfee’s vibrant interface and robust security features make it your ultimate security companion. From locking down your device to tracking its every move, McAfee Mobile Security ensures your device stays safe and secure.
More Anti-Theft Gems:
CrookCatcher: Snapshots of intruders in action, delivered straight to your inbox; free and ad-supported for an extra pop of Security.
Prey : is a colorful cross-platform tracker with free and premium versions, offering a rainbow of device protection options.Where’s My Droid: Find your phone in a burst of colors with GPS tracking, remote ringing, and SIM change alerts; free version with premium upgrade options for extra sparkle.
Wrapping up
Preventing thieves from taking control of your phone and online account requires a multi-faceted approach. Understanding the limitations of common security measures, using tools like Hammer Security, activating Find My Device or Find My iPhone, downloading antivirus software, using a VPN on public Wi-Fi networks, and backing up your data regularly are all essential steps in protecting your devices and personal information.
By taking these measures, you can significantly reduce the risk of thieves taking control of your phone and online accounts, giving you peace of mind in the long run.
While all of these might seem like a lot, as the saying goes, it’s better to be safe than to be sorry.

