
When it comes to Digital security and Privacy policy, the line between fiction and reality can sometimes blur. You would see something happen and Wonder, “Doesn’t this feel like a Movie?”
Take, for instance, the classic heist scene from the Movie Superman 3 (1983), where Richard Pryor’s character, Gus Gorman, goes from being down-and-out to an employed computer programmer. His newfound skills lead him to siphon off small amounts of money from various accounts, catching the attention of Ross Webster, CEO of Webster Industries.
What follows is a megalomaniacal crime spree involving missiles, kryptonite, and a red Ferrari 308, all orchestrated by Gorman under Webster’s guidance. While this may seem like a Hollywood fantasy, it serves as an early lesson about the importance of staff vetting, monitoring system and user activity, the dangers of insider threats, and the need for more advanced Digital security measures.
It’s 2024, and the need for protection against digital security threats is more prevalent than ever. The need for privacy policy has never been greater. This is especially true in light of recent events such as the rise of information-stealing malware, the challenges posed by the increasing number of connected devices in smart homes, and the evolving tactics of cyber criminals in phishing attacks.
As technology advances, so must our understanding of risks and the measures we take to mitigate them. This ultimate guide is an overview of F Secured, which aims to provide accessible insight into the world of digital security and privacy policy, drawing on the expertise of multiple experts in the field.
Let’s dig right in!
What is Digital Security?

“Digital security? Since so much of our lives today lives in cyberspace, like our banking, taxes, property ownership, car ownership, gun ownership, etc., it does not take much for a hacker to get into these records, monkey about, and suddenly our money is gone, stolen by cyber thieves, or our reputation is damaged because some cybercriminal has put false information into a system we use or on social media about us. There are many things a malicious hacker can do that would damage us. Thus, cyber security should be very important to all of us.” – Quora.
As mentioned above, digital security is crucial in safeguarding our digital lives, including sensitive information like banking, taxes, and personal data.
According to experts at McAfee, a leading authority in digital security, it is essential to prioritize cybersecurity measures to protect against malicious threats.
Ensuring Your Digital Security and Privacy is More Important than ever:
As highlighted by F-Secure, the average American household now boasts 22 connected IoT devices, a number expected to rise to 34 by 2025. While these devices offer convenience and efficiency, they also present new challenges in terms of security.
The infamous ‘Mirai’ botnet attack in 2016 is a stark reminder of the vulnerabilities inherent in IoT devices Mirai infected over 600,000 devices by exploiting weak or default passwords, turning them into bots to launch massive DDoS attacks. This incident underscores the urgent need for robust security measures to protect against such threats.
Cybercriminals are increasingly targeting IoT devices due to their widespread adoption and often inadequate security measures. As noted by Tom Gaffney from F-Secure’s Connected Home Security initiative, these devices are prime targets for malicious actors seeking to compromise sensitive information or launch large-scale attacks. With nation-state attacks rising, the need for digital solid security practices is more critical than ever.
Hence, digital security, as defined by experts like Nick Espinosa, revolves around identifying vulnerabilities and potential exploits. Espinosa, Chief Security Fanatic, emphasizes the necessity of recognizing that if there’s a vulnerability, someone will exploit it. This highlights the importance of proactive security measures and constant vigilance in safeguarding against cyber threats.
5 Key Topics Covered in the F-Secured Digital Guide:
- Malware and Infostealers
- Security and the Smart Home
- Mastering Your Passwords
- Phishing Scam
- key scam alerts that demand our attention
1. Malware and Infostealers:
According to the F-Secure guide, the rise of connected IoT devices has brought about a new era of convenience and efficiency but also increased concerns about digital security. As cyber threats become more sophisticated, protecting these devices from malware and information thieves has become a top priority.
Malware, short for malicious software, refers to any software designed to damage, disrupt, or gain unauthorized access to a computer system. One of the most common types of malware is the ‘infostealer,’ which targets explicitly sensitive information such as login credentials and personal data. These threats are often delivered through phishing emails, malicious websites, or compromised software.
In recent years, the prevalence of malware and info stealers has grown significantly, posing a serious risk to individuals and organizations. Cybercriminals use these tools to steal sensitive information, compromise systems, and disrupt operations. For example, the ‘Mirai’ botnet attack in 2016 infected hundreds of thousands of IoT devices, highlighting their vulnerability to malware attacks.
To protect against malware and info stealers, it is essential to implement robust security measures. This includes keeping software and systems up to date, using strong and unique passwords, and being cautious of suspicious emails or links. Additionally, antivirus software and firewalls can help detect and prevent malware infections.
2. Security and the Smart Home:
As pointed out, the proliferation of connected devices in modern homes, expected to reach 34 per household by 2025, presents many challenges for consumers, hardware manufacturers, and communication service providers (CSPs). This surge in connected devices has revolutionized the concept of smart homes, offering convenience and efficiency but also raising serious security concerns.
Deloitte’s research indicates that there are currently 22 connected IoT devices in the average American home, a number expected to rise steadily. This exponential growth in IoT devices has created a complex network of vulnerabilities that cybercriminals can exploit. The infamous ‘Mirai’ botnet attack in 2016, which compromised over 600,000 IoT devices, is a vivid reminder of the security risks associated with smart homes.
To address these challenges, experts like Tom Gaffney from F-Secure emphasize the critical need for robust security measures in the connected home. Gaffney underscores the importance of protecting IoT devices from cyber threats, highlighting consumers and CSPs’ unique challenges.
One key challenge is ensuring that IoT devices are secure by design, with built-in security features that can withstand evolving cyber threats. This requires collaboration between hardware manufacturers and security experts to develop and implement effective security measures.
Additionally, the rapid evolution of IoT technology has led to the adoption of innovative solutions like containerization and virtualization. These technologies offer new opportunities for enhancing security in the smart home environment. By isolating IoT applications in secure containers, vulnerabilities can be minimized, and the impact of potential breaches can be mitigated.
However, despite these advancements, the security landscape of smart homes remains complex and ever-changing. Cybercriminals are constantly evolving their tactics to exploit vulnerabilities in IoT devices, making it essential for consumers and CSPs to stay vigilant and proactive in their security practices.
This might sound gibberish to a non-Cyber savvy audience, so it needs some unpicking.
Set your mind to your home filled with smart devices like smart thermostats, security cameras, and voice assistants. These devices make life easier but also create security risks. Think of it like having many doors in your home; a burglar can get in if one isn’t locked.
Experts say around 22 of these smart devices are in the average American home, and this number is growing fast. But with more devices, there are more ways for hackers to break in, just like how more doors mean more ways for burglars to get into your house.
In the past, a big cyberattack called the ‘Mirai’ botnet hacked over 600,000 smart devices. This showed how vulnerable our homes can be to cybercriminals.
Experts like Tom Gaffney from F-Secure say we need to ensure our smart devices have strong security features to make our homes safer. This is like adding strong locks to all the doors in your home to keep burglars out.
New technologies like containers and virtualization can also help by creating secure spaces in which our smart devices can operate. It’s like putting each of your valuables in a safe, so even if one gets stolen, the others are still protected.
However, despite these improvements, we must stay alert because hackers are always finding new ways to break in. Just like we lock our doors and windows to keep our homes safe, we need to take steps to protect our smart devices, too.
3. Mastering Your Password
Another point from the F-secure guide is Mastering your password.
As our digital footprint expands, so does the number of online accounts we manage. From banking and shopping to social media and email, we constantly create new accounts across various platforms. However, the convenience of having multiple accounts comes with a significant challenge remembering all the passwords.
Many people resort to using a handful of passwords across different accounts or slightly changing a common password to address this challenge. This practice, while seemingly convenient, poses a severe security risk. Cybercriminals are adept at exploiting weak passwords through credential stuffing, using leaked credentials from one service to gain unauthorized access to other accounts.
Moreover, storing passwords in web browsers, while convenient, has its risks. Cybercriminals have targeted browsers with ‘infostealer’ malwares, aiming to steal login credentials stored within them. This underscores the importance of using strong, unique passwords for each account and avoiding reusing passwords across multiple services.
One recommended approach to password security is using passphrases—combinations of words that are easier to remember yet difficult for attackers to guess. Passphrases balance security and usability, providing a stronger alternative to traditional passwords.
Despite the benefits of passphrases, managing a large number of them can be challenging. This is where password managers come in. Password managers generate strong, unique passwords for each account and securely store them, eliminating users needing to remember multiple passwords. Additionally, password managers can alert users to potential security breaches, providing an added layer of security.
In summary, mastering the password is a critical aspect of digital security. Individuals can significantly enhance their online security posture by using strong, unique passwords or passphrases and leveraging password managers. As digital threats evolve, adopting secure password practices remains essential to safeguarding personal and sensitive information online.
4. Phishing scam
Another critical aspect of digital security highlighted in the F-Secure guide is the prevalence and impact of phishing attacks. These malicious campaigns often exploit current events and human emotions to trick individuals into divulging sensitive information or engaging in fraudulent activities.
One example discussed is the ‘Hi Mum’ scam, a form of smishing where scammers pose as the recipient’s adult child in urgent need of financial assistance. By preying on parental instincts, scammers aim to deceive victims into sending money or personal information, leading to substantial financial losses.
To avoid falling victim to phishing scams like the ‘Hi Mum’ scam, individuals should be cautious of unsolicited messages, especially those requesting urgent financial help or offering unrealistic rewards. Verifying the sender’s identity through other means, such as contacting them directly or through social media, can help confirm the request’s legitimacy.
Additionally, it’s essential to educate oneself and others about the common tactics used in phishing attacks, such as fake charity solicitations or promises of free items or services. By remaining vigilant and practicing good cybersecurity habits, individuals can protect themselves against the threats posed by phishing scams and other forms of cybercrime.
Another scam highlighted in the F-Secure guide is the gaming-related phishing scams, which target the vast gaming community and their valuable accounts. These scams exploit the popularity of gaming platforms like Steam and Roblox, enticing users with promises of free in-game currency or items.
One tactic mentioned is the ‘voting scam’ targeting Steam users, where attackers deceive victims into visiting phishing websites under the guise of supporting a gaming team. Once on these fraudulent sites, users unknowingly provide their login credentials, enabling attackers to hijack their Steam accounts.
Similarly, Roblox users are targeted through enticing offers of free Robux and premium memberships. Scammers use YouTube videos and fake advertisements to lure unsuspecting players to phishing websites, where they are prompted to enter their account credentials, leading to account takeover.
To protect against gaming-related phishing scams, individuals should exercise caution when encountering unsolicited offers or links promising free virtual currency or items. Implementing security measures such as safe browsing protection and avoiding entering login credentials outside of official gaming platforms can help mitigate the risk of falling victim to these scams.
Furthermore, educating gamers, especially younger ones, about the dangers of phishing and the importance of verifying the legitimacy of offers can go a long way in safeguarding their accounts and personal information. By staying informed and vigilant, gamers can enjoy their favorite pastime without falling prey to cybercriminals’ schemes.
3 Key scam alerts on Digital Security that demand our attention:

As we peer into the digital landscape of 2023, F-Secure experts foretell three key scam alerts that demand our attention:
1. Persistent Phishing and Smishing Scams:
First and foremost, phishing and smishing scams are anticipated to persist and adapt. Cybercriminals are capitalizing on vulnerabilities with the rise of remote work and the proliferation of connected devices in our homes. Recent surveys indicate a concerning trend, with a significant portion of consumers falling victim to phishing attempts impersonating trusted entities like banks and insurance companies. It’s imperative to exercise caution when encountering unsolicited messages, especially those soliciting sensitive information or financial transactions.
2. Escalating Account Takeover Attacks:
Next on the radar is the looming threat of account takeover attacks. Criminals are poised to leverage extortion tactics akin to those seen in ransomware incidents, targeting individuals’ social media profiles, email accounts, and cloud storage. The potential consequences are dire, ranging from data exposure to outright deletion of accounts. As employees increasingly access sensitive data from home, bolstering security measures becomes paramount to thwarting such attacks.
3. Increasing Threats Targeting Gamers:
Furthermore, gamers are anticipated to face escalating threats in the digital realm. Cybercriminals see fertile ground for exploitation with the gaming industry experiencing exponential growth. Personal information gleaned from gaming platforms holds significant value in the dark market, facilitating various nefarious activities such as identity theft and financial fraud. As phishing attempts proliferate across email, text messages, and social media, gamers must remain vigilant against deceptive tactics.
Safeguarding Your Digital Security With Privacy Tools:
Having explored the insights provided by the F-Secure Guide on digital security, it’s evident that the digital landscape is fraught with numerous threats to our Privacy and security. With cyber threats looming around every corner, it’s essential to arm yourself with the right tools to protect your personal information from prying eyes. By incorporating a range of privacy tools into your online habits, you can fortify your defenses and mitigate the risks associated with Digital Security Bridge.
Below are 4 Privacy Tools to Safeguard your Digital data:
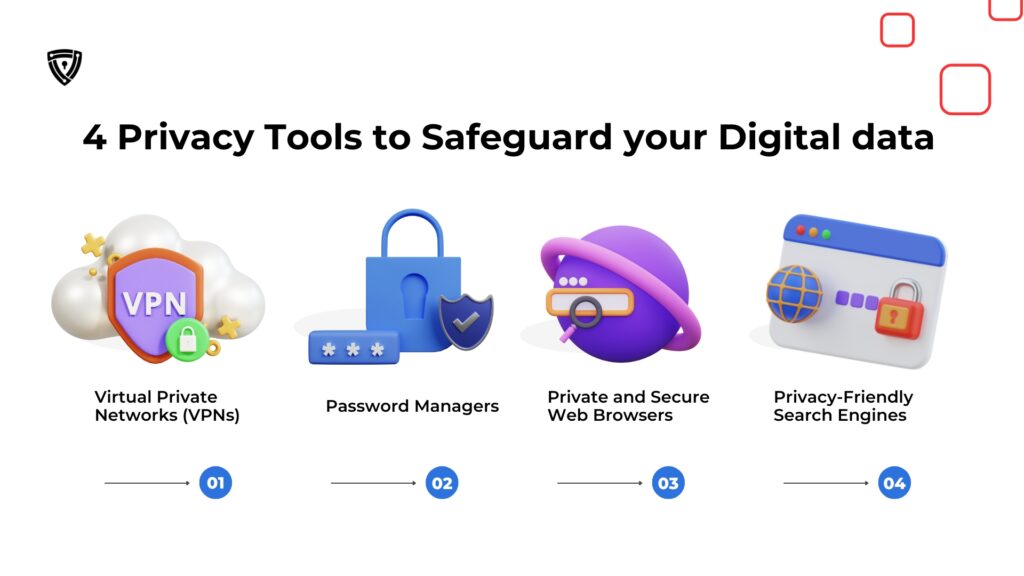
- Virtual Private Networks (VPNs): As the digital world becomes increasingly interconnected, Virtual Private Networks (VPNs) emerge as a crucial tool for preserving online Privacy. By encrypting your internet traffic and masking your IP address, VPNs shield your online activities from prying eyes. Whether you’re browsing on public Wi-Fi or accessing sensitive information, VPNs offer a layer of security that is indispensable in today’s digital age. With reputable VPN services like ProtonVPN and NordVPN, you can browse the web confidently, knowing that your data remains secure and inaccessible to cybercriminals.
- Password Managers: In the battle for digital security, strong and unique passwords are your first line of defense against unauthorized access to your accounts. However, managing a multitude of passwords can be daunting. This is where password managers come to the rescue. These tools generate complex passwords and securely store them, ensuring that your accounts remain protected from potential breaches. With options like Bitwarden and 1Password, you can easily take control of your passwords and safeguard your online identity.
- Private and Secure Web Browsers: Your choice of web browser plays a pivotal role in preserving your online Privacy. While mainstream browsers like Google Chrome and Safari offer convenience, tracking your online activities may compromise your Privacy. You can browse the web without sacrificing your Privacy by opting for privacy-focused browsers like Brave or Tor. These browsers prioritize user privacy by blocking intrusive trackers and offering features like built-in ad blockers and support for the Tor network. With Brave and Tor, you can browse the internet with peace of mind, knowing that your online activities remain private and secure.
- Privacy-Friendly Search Engines: Search engines serve as gateways to the vast expanse of the internet, but they also pose a threat to your Privacy by collecting and monetizing your search data. To safeguard your Privacy while searching the web, consider using privacy-friendly search engines like DuckDuckGo and MetaGer. These search engines prioritize user privacy by refraining from tracking your search history or collecting personal information. With DuckDuckGo and MetaGer, you can explore the internet without leaving a digital footprint, ensuring that your online searches remain private and anonymous.
Additional Privacy Measures: In addition to employing privacy tools, there are further steps you can take to bolster your digital security and Privacy.

- Deleting your data from corporate databases.
- Monitoring for data breaches.
- Removing yourself from data brokers is a proactive measure that can minimize your digital footprint and reduce the risk of unauthorized access to your personal information.
By embracing these additional privacy measures, you can effectively enhance your online security and safeguard your digital Privacy.
Conclusion
In conclusion, by embracing a holistic approach to digital security and Privacy and incorporating the Privacy above tools into your online routine, you can navigate the digital landscape with confidence and peace of mind. With vigilance and the right tools, you can protect your personal information from cyber threats and maintain control over your online Privacy.

